信息收集
踩点
攻击者对某个组织进行有计划,有步骤的踩点,收集整理出一份关于该组织的安全剖析图
因特网踩点
- web网页
- 相关组织
- 地理信息
- 员工信息
- 近期重大事件
- 安全策略
- 搜索引擎
whois
- 通过whois,可以查询到域名拥有者信息
DNS
- 通过nslookup查询该组织的相关dns服务器信息
网络侦查
- traceroute可以侦查到目的主机传输路径经过的网际跳远
扫描
使用扫描来发现目标系统有哪些服务对外监听以及能直接从因特网访问
ARP主机发现
- 使用arp-scan
- arp-scan时在局域网内最合理最快的扫描工具
my@my-PC:~$ sudo arp-scan 192.168.43.0/24
Interface: wlp3s0, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9 with 256 hosts (http://www.nta-monitor.com/tools/arp-scan/)
192.168.43.1 82:92:e3:d0:7f:d4 (Unknown)
1 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9: 256 hosts scanned in 2.531 seconds (101.15 hosts/sec). 1 responded
- 使用nmap也能同样进行扫描
sudo nmap -sn -PR 192.168.43.0/24
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 09:00 CST
Nmap scan report for 192.168.43.1
Host is up (0.0047s latency).
MAC Address: 82:92:E3:D0:7F:D4 (Unknown)
Nmap scan report for 192.168.43.242
Host is up.
Nmap done: 256 IP addresses (2 hosts up) scanned in 3.82 seconds
ICMP主机发现
ICMP协议是一种面向无连接的协议,用于传输出错报告控制信息。它是一个非常重要的协议,它对于网络安全具有极其重要的意义
响应报文
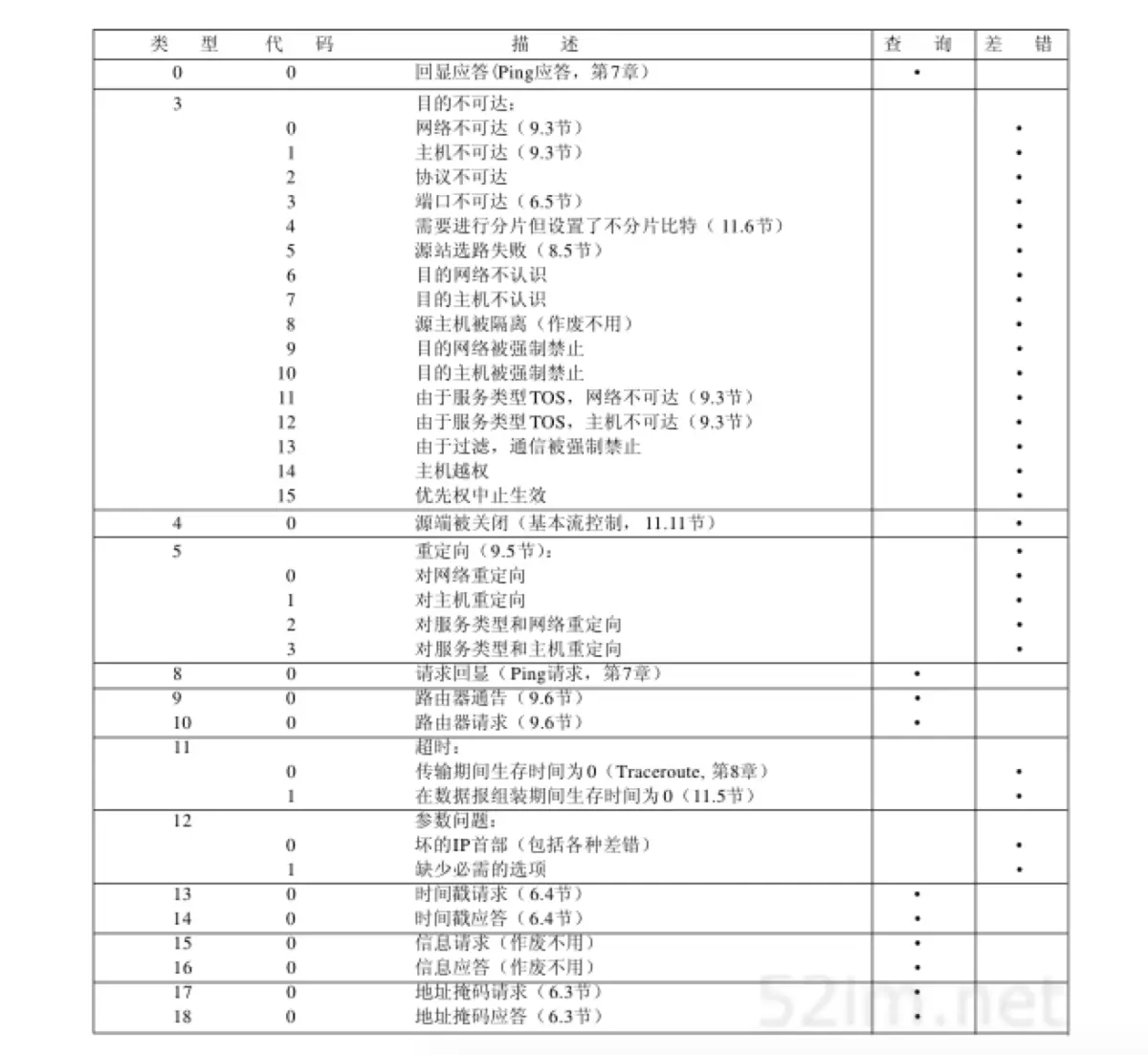
使用ping
使用nmap扫描
my@my-PC:~$ sudo nmap -sn -PE zbq.ismy.wang
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 10:04 CST
Nmap scan report for zbq.ismy.wang (120.79.6.172)
Host is up (0.067s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.43 seconds
- 使用hping
my@my-PC:~$ sudo nping -c 2 --icmp --icmp-type time zbq.ismy.wang
Starting Nping 0.7.40 ( https://nmap.org/nping ) at 2019-12-09 10:07 CST
SENT (0.0627s) ICMP [192.168.43.242 > 120.79.6.172 Timestamp request (type=13/code=0) id=52393 seq=1 orig=0 recv=0 trans=0] IP [ttl=64 id=34535 iplen=40 ]
SENT (1.0630s) ICMP [192.168.43.242 > 120.79.6.172 Timestamp request (type=13/code=0) id=52393 seq=2 orig=0 recv=0 trans=0] IP [ttl=64 id=34535 iplen=40 ]
Max rtt: N/A | Min rtt: N/A | Avg rtt: N/A
Raw packets sent: 2 (80B) | Rcvd: 0 (0B) | Lost: 2 (100.00%)
Nping done: 1 IP address pinged in 2.09 seconds
- windows 下可以使用superScan
TCP/UDP主机发现
- 使用nmap
my@my-PC:~$ nmap -Pn 192.168.43.1
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 10:11 CST
Nmap scan report for 192.168.43.1
Host is up (0.026s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
53/tcp open domain
Nmap done: 1 IP address (1 host up) scanned in 0.46 seconds
- 只扫描开启特定端口的主机
my@my-PC:~$ sudo nmap -Pn -sS -p 53 192.168.43.0/24
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 10:13 CST
Nmap scan report for 192.168.43.1
Host is up (0.0079s latency).
PORT STATE SERVICE
53/tcp open domain
MAC Address: 82:92:E3:D0:7F:D4 (Unknown)
Nmap scan report for 192.168.43.242
Host is up (0.000052s latency).
PORT STATE SERVICE
53/tcp closed domain
Nmap done: 256 IP addresses (2 hosts up) scanned in 4.36 seconds
- 使用nping
my@my-PC:~$ sudo nping -c 2 --tcp -p 53 --flags syn 192.168.43.1
Starting Nping 0.7.40 ( https://nmap.org/nping ) at 2019-12-09 10:14 CST
SENT (0.0368s) TCP 192.168.43.242:30555 > 192.168.43.1:53 S ttl=64 id=55281 iplen=40 seq=2174361648 win=1480
RCVD (0.2232s) TCP 192.168.43.1:53 > 192.168.43.242:30555 SA ttl=64 id=0 iplen=44 seq=2937135821 win=65535 <mss 1460>
SENT (1.0373s) TCP 192.168.43.242:30555 > 192.168.43.1:53 S ttl=64 id=55281 iplen=40 seq=2174361648 win=1480
RCVD (1.2432s) TCP 192.168.43.1:53 > 192.168.43.242:30555 SA ttl=64 id=0 iplen=44 seq=2952774060 win=65535 <mss 1460>
Max rtt: 205.814ms | Min rtt: 186.441ms | Avg rtt: 196.127ms
Raw packets sent: 2 (80B) | Rcvd: 2 (88B) | Lost: 0 (0.00%)
Nping done: 1 IP address pinged in 1.28 seconds
预防
- 密切留意ping活动
- 根据需求决定放行哪些ICMP请求
端口扫描
端口扫描是指某些别有用心的人发送一组端口扫描消息,试图以此侵入某台计算机,并了解其提供的计算机网络服务类型(这些网络服务均与端口号相关)
sS (TCP SYN扫描)
这种扫描也叫做半开扫描,不会建立一条tcp连接,所以很隐蔽
my@my-PC:~$ sudo nmap -sS 192.168.43.1
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 10:26 CST
Nmap scan report for 192.168.43.1
Host is up (0.050s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
53/tcp open domain
MAC Address: 82:92:E3:D0:7F:D4 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 1.95 seconds
- 添加D选项,可以假冒其他源IP发送请求,混杂在扫描请求当中
my@my-PC:~$ sudo nmap -sS 192.168.43.1 -D 10.1.1.1
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 10:33 CST
Nmap scan report for 192.168.43.1
Host is up (0.062s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
53/tcp open domain
MAC Address: 82:92:E3:D0:7F:D4 (Unknown)
Nmap done: 1 IP address (1 host up) scanned in 5.55 seconds
- FTP反弹扫描
它允许用户连接到一台FTP服务器,然后要求文件送到一台第三方服务器。 这个特性在很多层次上被滥用,所以许多服务器已经停止支持它了。其中一种就是导致FTP服务器对其它主机端口扫描。 只要请求FTP服务器轮流发送一个文件到目标主机上的所感兴趣的端口。 错误消息会描述端口是开放还是关闭的。 这是绕过防火墙的好方法
使用netcat扫描
my@my-PC:~$ nc -v -z -w2 192.168.43.1 1-140
192.168.43.1: inverse host lookup failed: Unknown host
(UNKNOWN) [192.168.43.1] 53 (domain) open
预防
- 使用入侵检测系统(IDS)
- 关闭不必要服务
操作系统检测
- 使用nmap -O 选项,探测操作系统类型(主动式探测)
my@my-PC:~$ sudo nmap -O ip
Starting Nmap 7.40 ( https://nmap.org ) at 2019-12-09 16:25 CST
Nmap scan report for zbq.ismy.wang (120.79.6.172)
Host is up (0.070s latency).
Not shown: 990 filtered ports
...
Aggressive OS guesses: Linux 3.10 - 4.2 (91%), Linux 3.2 - 4.6 (90%), Linux 2.6.32 (89%), Linux 3.16 (89%), Linux 4.4 (88%), OpenWrt Kamikaze 7.09 (Linux 2.6.22) (88%), Linux 3.11 - 3.12 (87%), Linux 3.18 (87%), Crestron XPanel control system (87%), HP P2000 G3 NAS device (87%)
No exact OS matches for host (test conditions non-ideal).
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 81.44 seconds
查点
服务指纹分析
- 使用nmap
- 使用amap分析服务版本
漏洞扫描
- nessus
标语抓取
- netcat或telnet
my@my-PC:~$ netcat zbq.ismy.wang 80
ss
HTTP/1.1 400 Bad Request
Server: nginx/1.12.2
Date: Mon, 09 Dec 2019 08:41:25 GMT
Content-Type: text/html
Content-Length: 173
Connection: close
<html>
<head><title>400 Bad Request</title></head>
<body bgcolor="white">
<center><h1>400 Bad Request</h1></center>
<hr><center>nginx/1.12.2</center>
</body>
</html>
常用服务查点
- FTP
- 应该不再使用FTP服务
- telnet查点
- 应使用更安全的ssh替代
- smtp
- 应该不再使用
- dns
- 使用dig查询有关dns服务器的信息
- tftp
- tftp不够安全,没有提供任何认证手段,攻击者能获取到许多敏感文件
- finger
- HTTP查点
- SNMP查点
- BGP查点
- RPC查点,查看主机有哪些端口正在监听rpc
rpcinfo -p 127.0.0.1